As building control systems become part of the IoT, Bruno Johnson looks at the approach IP-BLiS is taking to security.
Building control systems are vulnerable to attack, both from within the building and from the outside. This means that building control systems must employ security frameworks that require all users and all equipment to be authenticated, by checking their identity and integrity.

Buildings are highly regulated, which means that those responsible for all stages of a building lifecycle are required to have a high degree of competence and accountability. This is especially true of building security, as this can have a direct impact on building safety.
IP-BLiS recognises the need for strong security
IP-BLiS is not a new entity, but a collection of existing organisations that started working together in 2020. IP-BLiS recognises that the need for strong security is paramount for building control systems. While IT systems and professionals may have received training in the area of IP (Internet Protocol) security, OT (Operational Technology) systems and professionals have often been overlooked in this regard. Moreover, the requirements for certification or compliance with regulatory frameworks are, in many cases, still being defined.

For example, the U.S. National Institute of Standards and Technology (NIST) provides guidance in the form of the NISTIR 8259 series. NISTIR 8259A is the Core Device Cybersecurity Baseline that focuses on technical device capabilities, while the NIST 8259B covers non-technical requirements such as documentation, information queries, information dissemination and education and awareness. Meanwhile, the European Commission (EC) has published the ETSI EN 303 645 requirement, which relates to thirteen categories of security, focussing on technical device capabilities and non-technical requirements.
Additionally, the EC has updated the Radio Equipment Directive (RED), which establishes the regulatory framework for obtaining the CE mark. The Commission adopted additional mandates for the RED covering devices that have the ability to communicate over the Internet; process personal, traffic or location data; or that process financial transactions. These provisions become mandatory on 1 August 2024. Similarly, the U.S. Federal Communications Commission (FCC) in June of 2021, released a 12-month notice of proposed rulemaking and notice of inquiry document with a focus on improving the adoption of cybersecurity best practices.
Common provisions for security
The regulations and requirements for security can be distilled down to seven common provisions, as shown in the figure below.
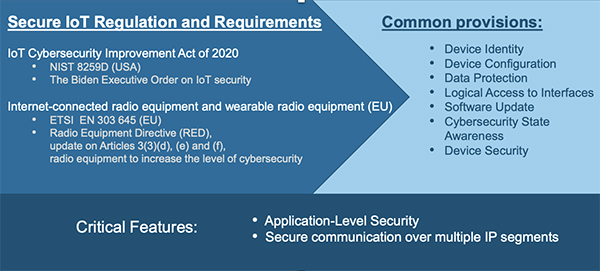
The common provisions are defined as follows:
• Device identity – a unique address value associated with a device or endpoint.
• Device configuration – the ability to configure devices through logical interfaces.
• Data protection – the ability to cryptographically protect a device and its stored data.
• Logical access – the ability to establish authentication and identification configuration.
• Software update – the ability to update a device’s software.
• Cybersecurity State Awareness – the ability to generate, monitor and report events.
• Device security – the ability to secure the device during normal operation.
Consideration at every phase of the building lifecycle
As well as the common device security provisions outlined above, the building control system must be able to handle device commissioning and decommissioning. A vulnerability submission handling process is also required, so that devices that have an identified vulnerability can be isolated and updated. Similarly, EoL (End of Life) and EoS (End of Service) policies should be in place to handle devices and systems that are no longer supported by their respective manufacturers. Hence security should be considered at every phase of the building lifecycle.
Of course in much of the world, there is relatively little new-build infrastructure. Hence it is anticipated that, as with IT systems, building control systems need to be continuously maintained and upgraded for security. As such, the provisions above need to be considered on a regular basis.
The benefits of following IP-BLiS recommendations
As explained, legislators are beginning to make security a mandatory requirement for some types of devices, and as such failure to comply with such security requirements could cause financial and reputational damage. Moreover, a security breach could cause secondary damage, such as safety.
IP-BLiS has outlined a set of common best practices related to building security. These best practices cover different areas of building control network management including device addressing, service discovery, security, physical layer support, and infrastructure requirements. While not exhaustive, these go a long way in helping to educate and inform professionals in the buildings industry of future changes.
Conclusion
As well as a need for increased training of both IP and OT professionals in building security, the challenge that the industry currently faces is that there is a patchwork of regulations defined in different regions, with little clear guidance for certification or compliance.
IP-BLiS recognises that common choices and best practices are an essential ingredient in making more complex and feature-rich building automations systems sustainable and manageable. It has outlined a set of common best practices related to the IoT and building security, and will continue providing information on the progress of products following these concepts, as they come onto the market.
This article was contributed to IP-BLiS by Bruno Johnson, Chair OCF Marketing & Communications Work Group.