KNXtoday Editor, Yasmin Hashmi, previews the new free-of-charge 30-minute training for anyone about to enrol on a certified KNX Basic Course and needs to understand the fundamentals of system security.
Any communication technology is a target for hackers, and this includes home and building automation systems. The demand for smart home and smart building technology is increasing rapidly, and more and more applications and equipment are being added to installations and interconnected for remote access in order to offer a better user experience. Without proper protection, however, they can represent the most vulnerable point in an installation.
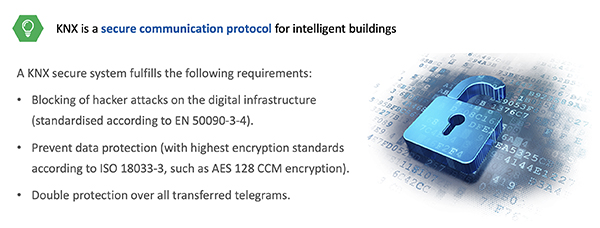
The KNX Association has been keenly aware of the need for security for some time, which is why it has taken strong measures to make its systems secure, including the introduction of KNX Secure that protects installations at an internal data level and external IP level. But how do you, as a KNX professional, use KNX Secure, and what strategies can you employ to ensure solid security of the systems you install?
How to prevent access to KNX installations
The new 30-minute ‘How to Prevent Access to KNX Installations’ online training from the KNX Association is free of charge and is available to all systems integrators with a MyKNX account. The course is an ideal complement to the ETS eCampus and is strongly recommended before enrolling on a certified KNX Basic Course. Those who complete the course will be given an official certificate.

The course will be structured in 4 chapters:
• Fundamentals
• Hacking scenarios & KNX system configurations
• Security measures
• Security recommendations.
Fundamentals
This chapter explores which areas are particularly vulnerable, such as systems that handle critical information, for example access codes, video door phones, door/window contact status, etc, as well as remote access applications for monitoring, maintenance and remote control. It goes on to explain how KNX technology has always followed all necessary security regulations, and how KNX Secure guarantees maximum security by offering a double protection through:
• KNX IP Secure – which extends the IP protocol in such a way that all transferred telegrams and data are completely encrypted.
• KNX Data Secure, which effectively protects user data against unauthorised access and manipulation by means of encryption and authentication.
Potential risks & KNX system configurations
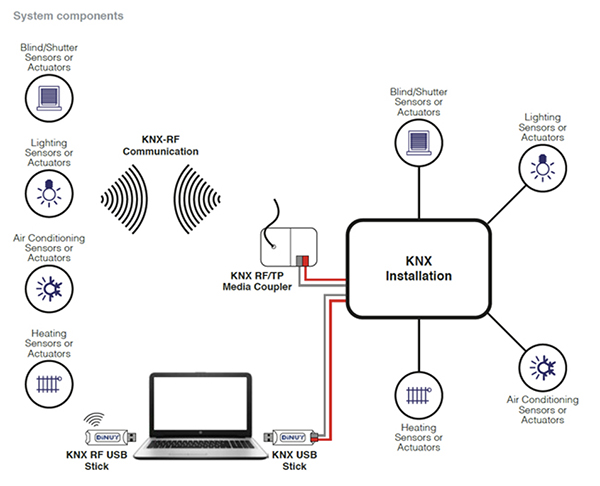
This chapter examines different potential risks and strategies to deal with them. It looks at preventing unauthorised access, whether physical or electronic for different types of design and installation, including:
• A KNX twisted-pair (TP) cable installation without any Internet connection.
• A KNX TP installation connected to the Internet through a physical connection to a computer (normally via USB) that acts as gateway.
• A KNX TP installation connected directly to the Internet through a router.
• A KNX RF installation.
Security measures
This chapter covers the security measures recommended for TP installations, IP installations and installations with Internet access. It also explains how to limit unwanted communication through couplers and routers, how to protect unwanted configuration reading/modification, and how to protect runtime communication.
Security recommendations
This section summarises the steps that can be taken to secure your KNX installation, including:
• If an installation is linked to Internet, the use of a VPN tunnel for accessing is an absolute MUST.
• When using KNX Secure tunnelling, use the strong passwords suggested by ETS and do not replace them with weak ones.
• Special attention is needed for installations in public areas without any surveillance – even a wired KNX system can be vulnerable to attack.
• Installations using wireless communication are completely out in the open. The use of KNX Secure with this medium is highly recommended.
• If you have a KNX IP backbone and other IP networks, use VLAN separation and allow communication only via a suitable firewall.
• Avoid the unauthorised access to the bus cables with physical protection.
• Set a strong password in the ETS Project to protect the configuration.
• Set a strong password for your router.
• Use firewalls to manage the IP communication.
• Use VPN connection for Internet access.
• Disable Multicast address and port 3671 (ETS).
• Set the authentication in visualisation services and redirect the port 80 for it.
Registration
To benefit from the full course, register free of charge by going to your MyKNX account and following the link to ‘Online Courses’.
Yasmin Hashmi is the Editor of KNXtoday magazine.